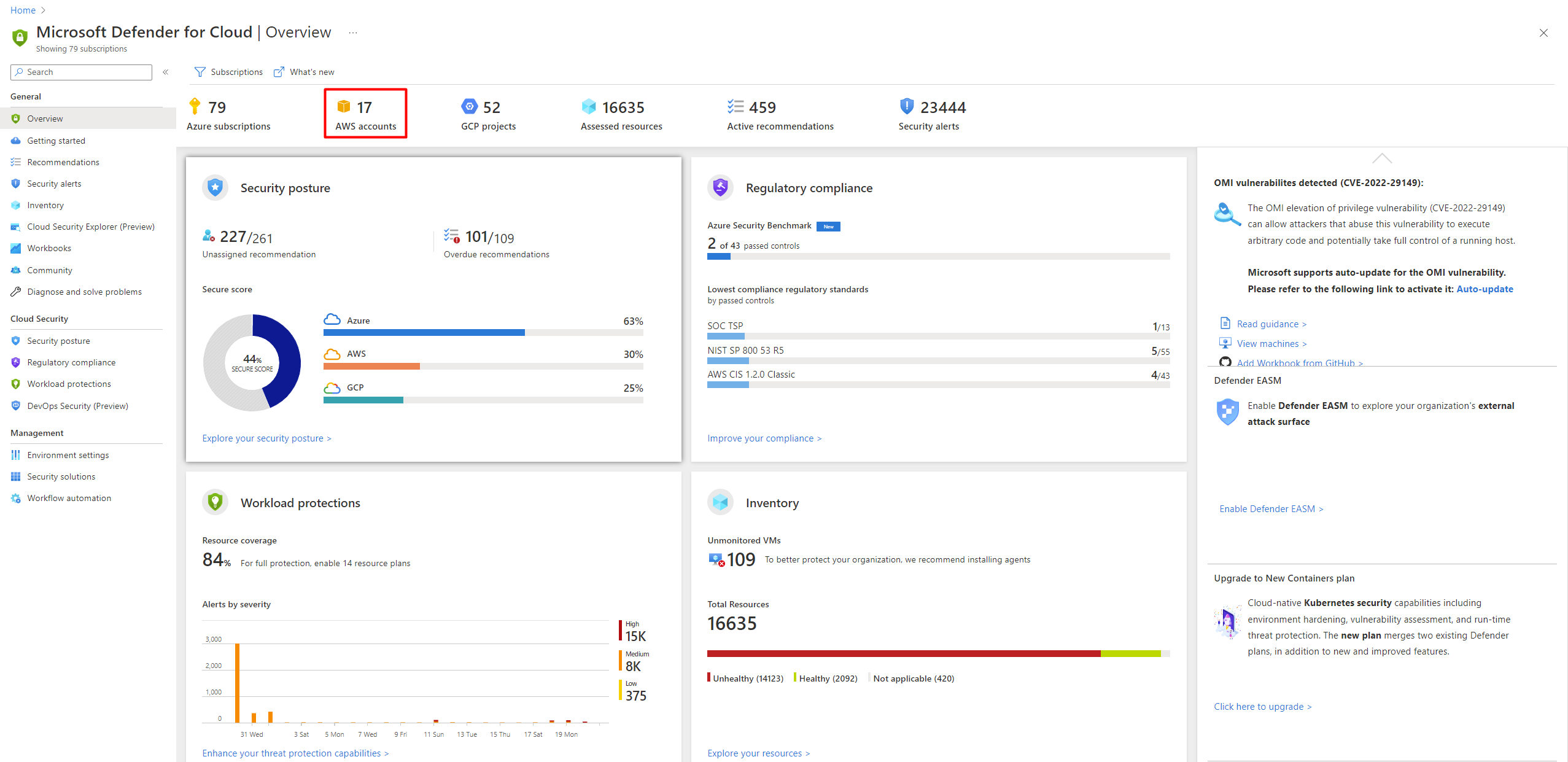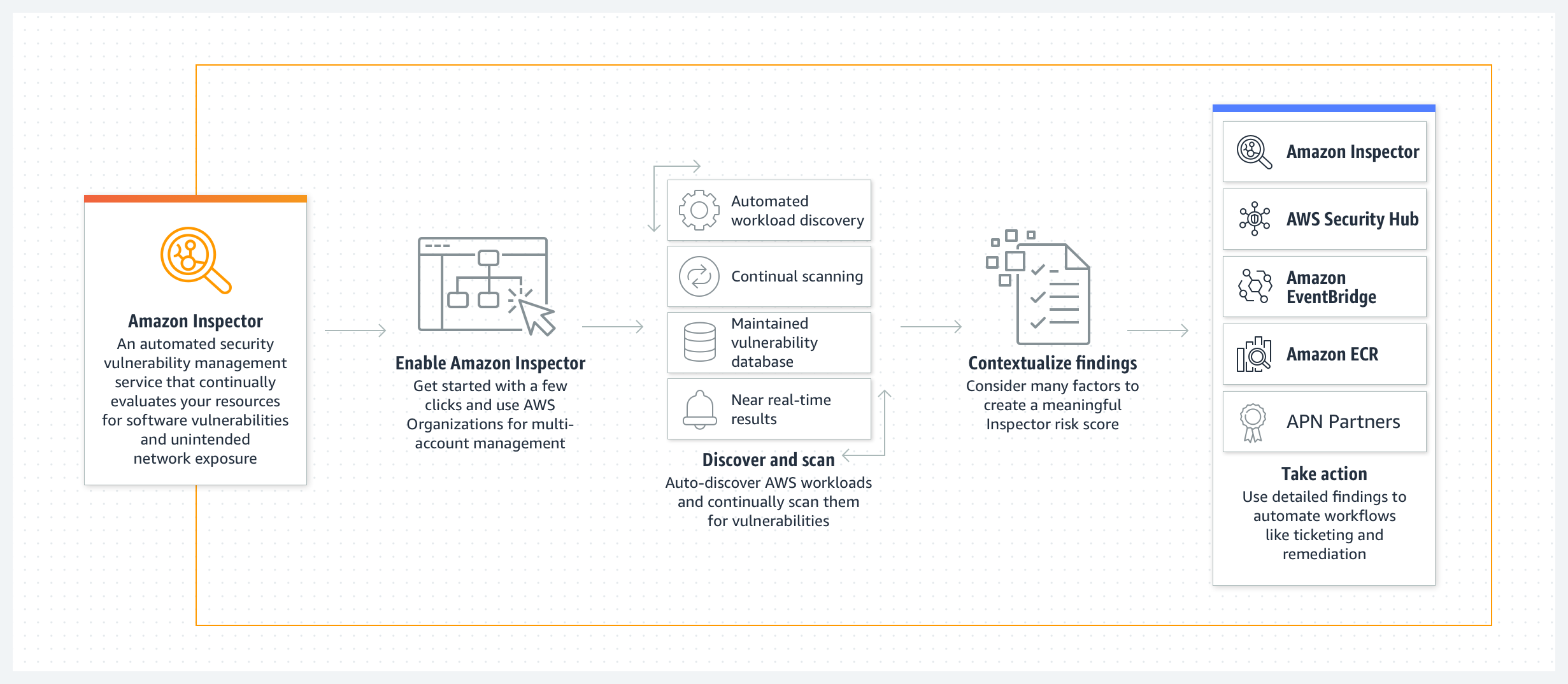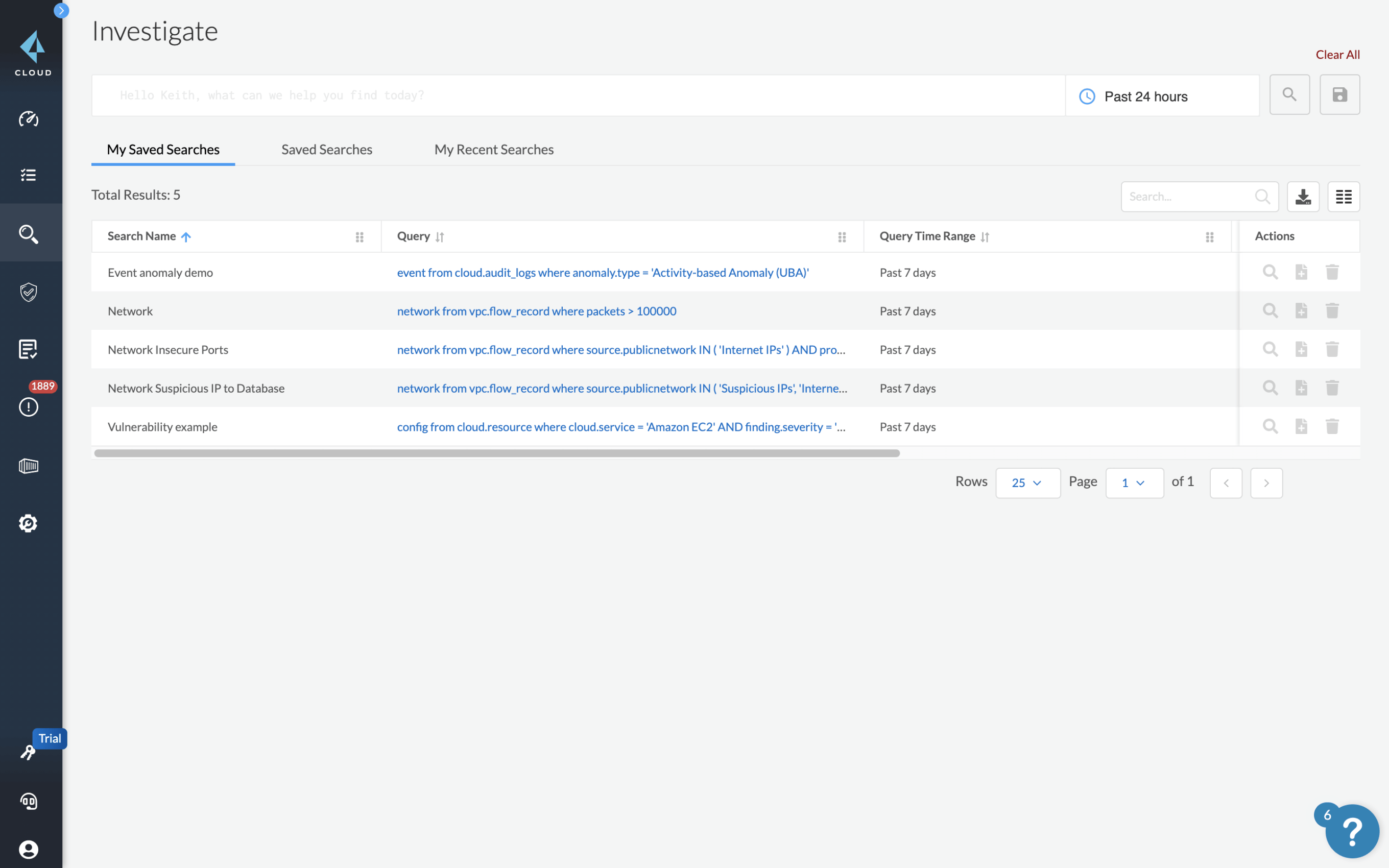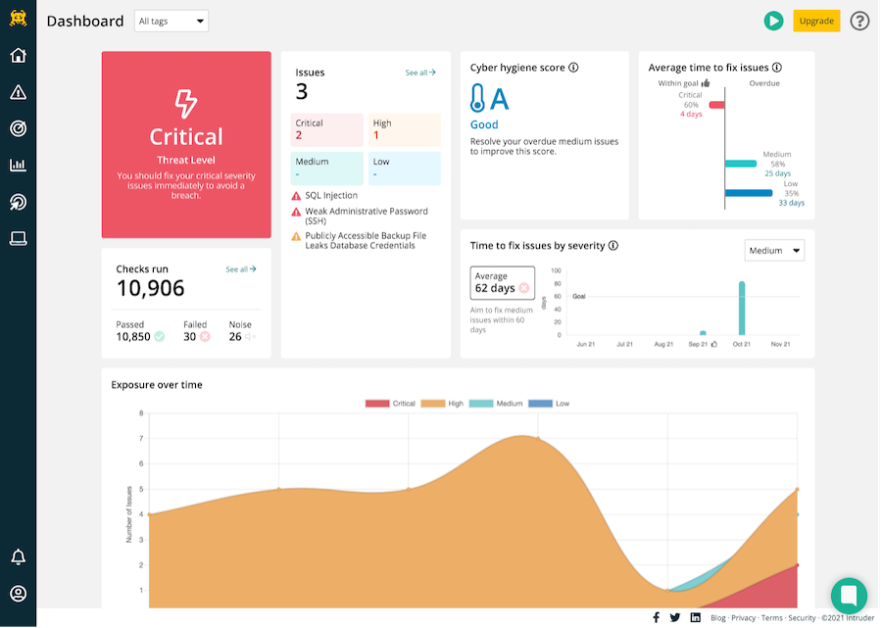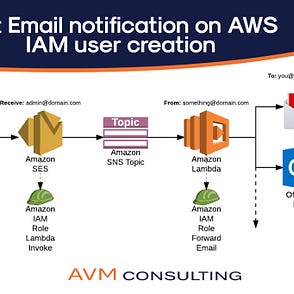
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium
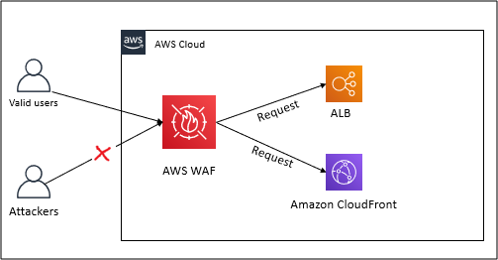
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium